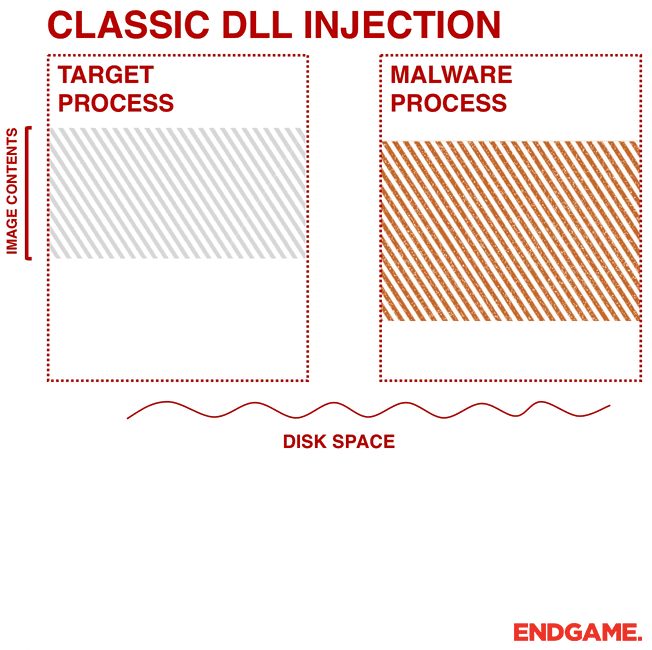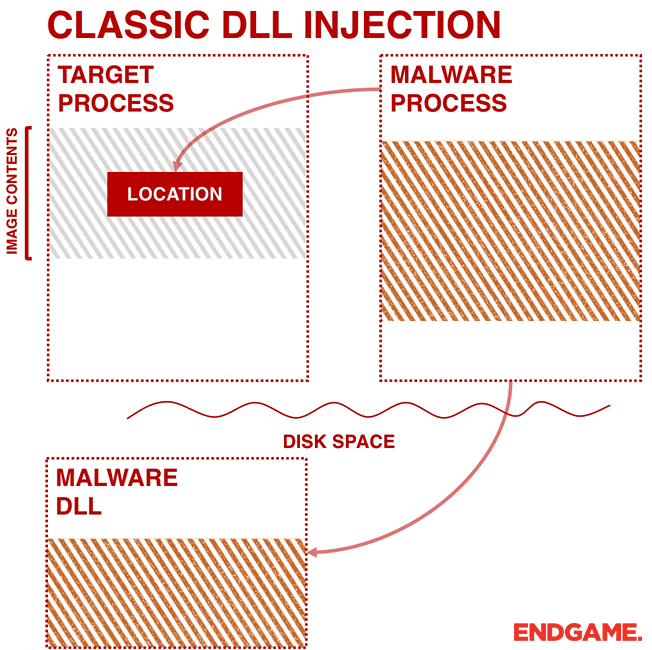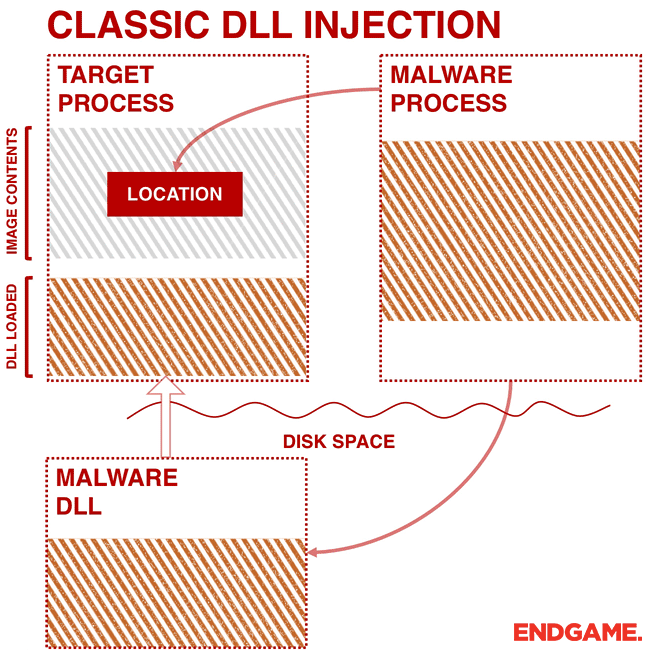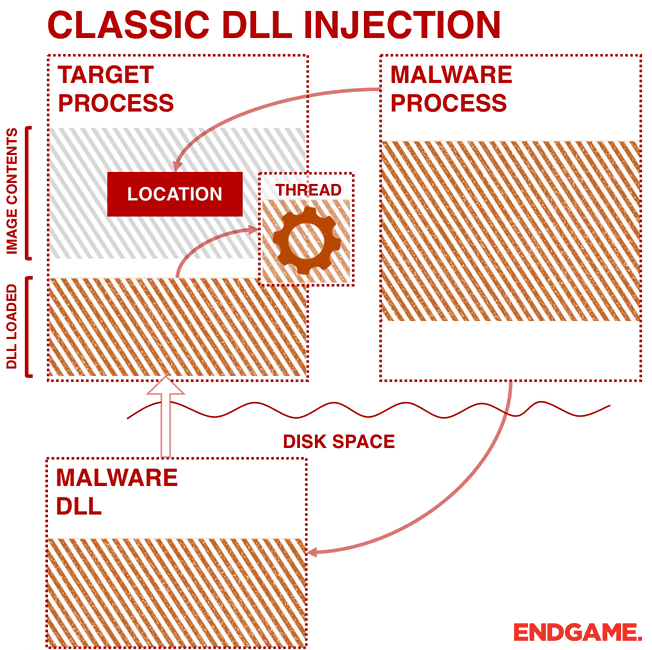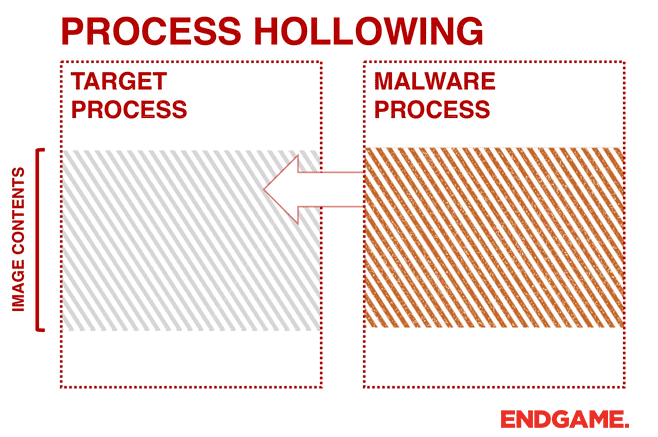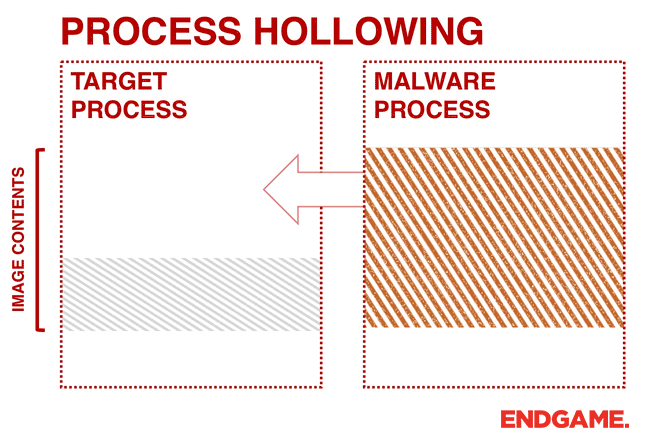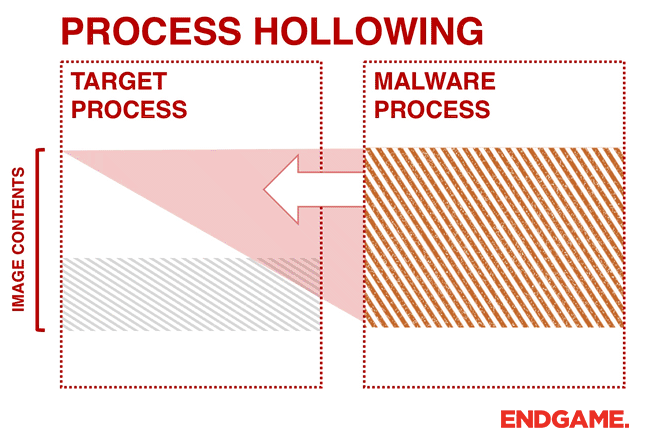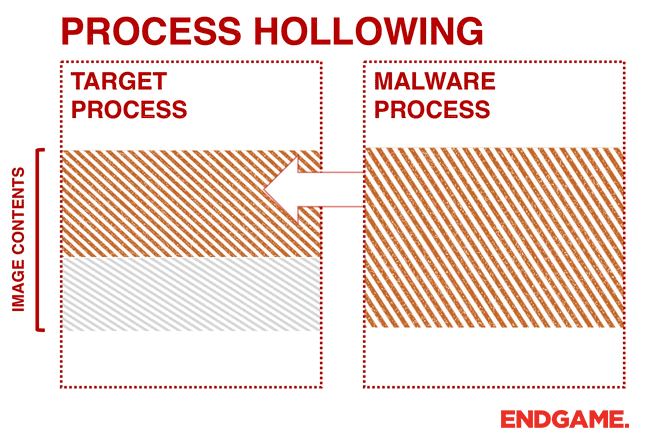
Ten process injection techniques: A technical survey of common and trending process injection techniques | Elastic Blog
![Cisco Identity Services Engine Administrator Guide, Release 3.2 - Basic Setup [Cisco Identity Services Engine] - Cisco Cisco Identity Services Engine Administrator Guide, Release 3.2 - Basic Setup [Cisco Identity Services Engine] - Cisco](https://www.cisco.com/c/dam/en/us/td/i/300001-400000/350001-360000/356001-357000/356761.jpg)
Cisco Identity Services Engine Administrator Guide, Release 3.2 - Basic Setup [Cisco Identity Services Engine] - Cisco
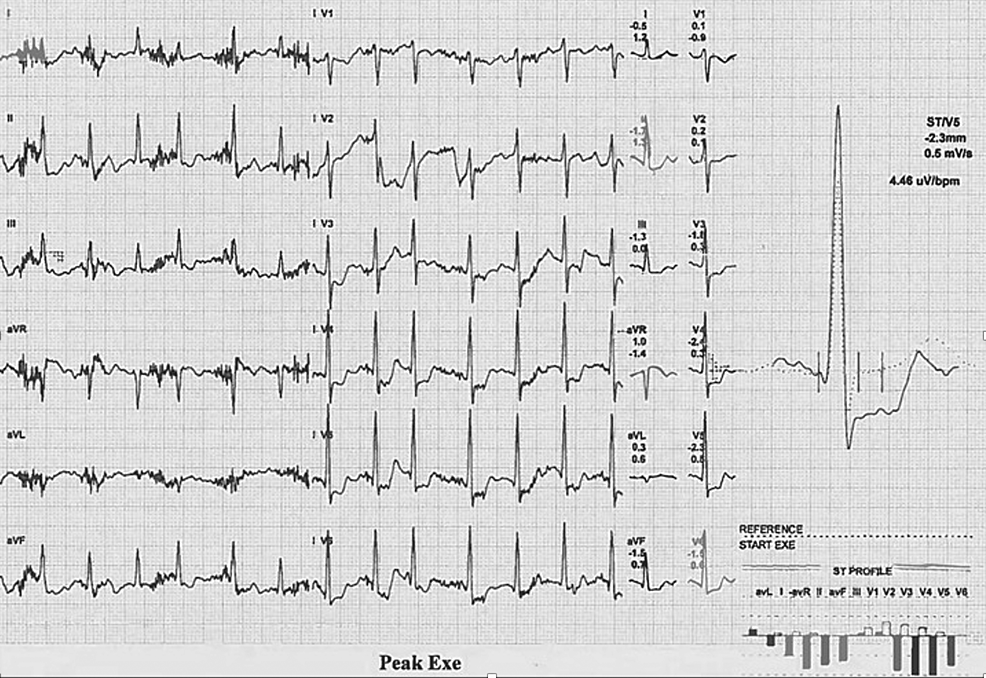
Cureus | Incidental Cardiovascular Abnormalities in the Abdominal Aortic Aneurysm (AAA) Surveillance Population During the AAA Get Fit Trial: A Case Series and Review of the Literature | Article
![Cisco Identity Services Engine Administrator Guide, Release 3.2 - Basic Setup [Cisco Identity Services Engine] - Cisco Cisco Identity Services Engine Administrator Guide, Release 3.2 - Basic Setup [Cisco Identity Services Engine] - Cisco](https://www.cisco.com/c/dam/en/us/td/i/300001-400000/350001-360000/356001-357000/356760.jpg)
Cisco Identity Services Engine Administrator Guide, Release 3.2 - Basic Setup [Cisco Identity Services Engine] - Cisco
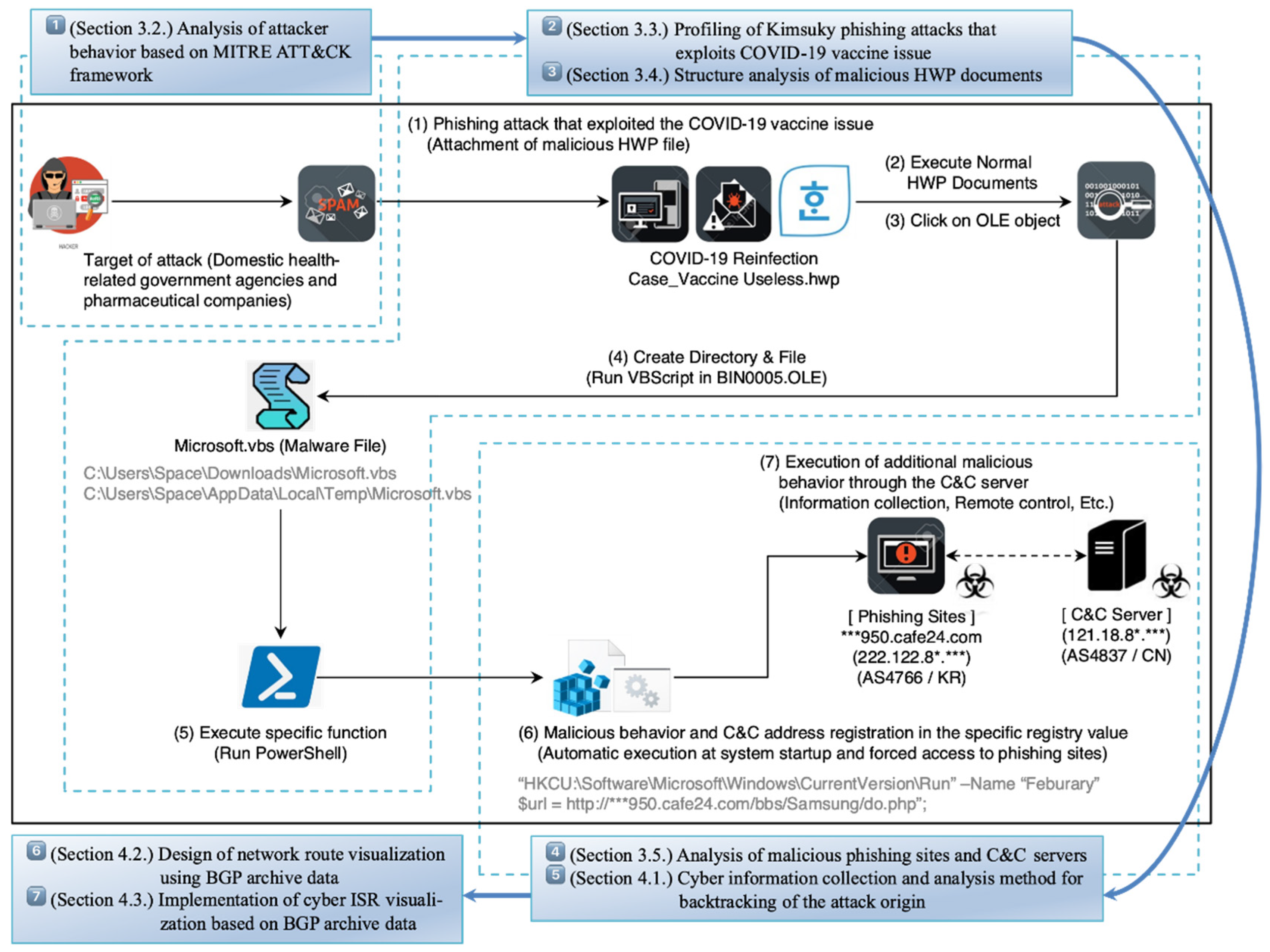
Electronics | Free Full-Text | Research on Cyber ISR Visualization Method Based on BGP Archive Data through Hacking Case Analysis of North Korean Cyber-Attack Groups

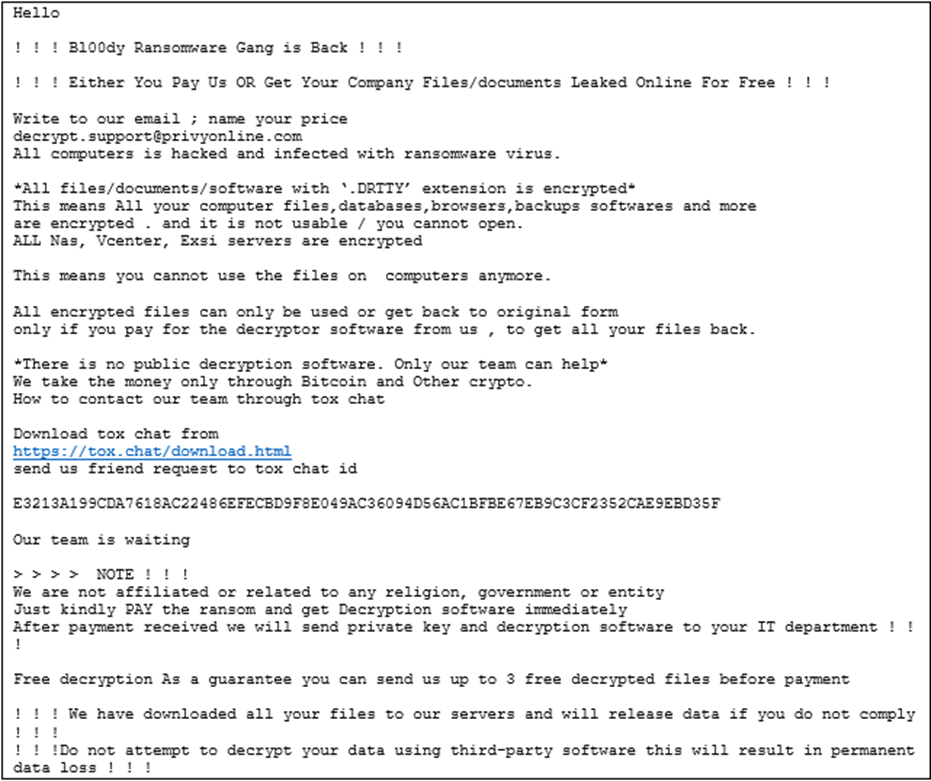
Netscaler Exploitation to Social Engineering: Mapping Convergence of Adversary Tradecraft Across Victims
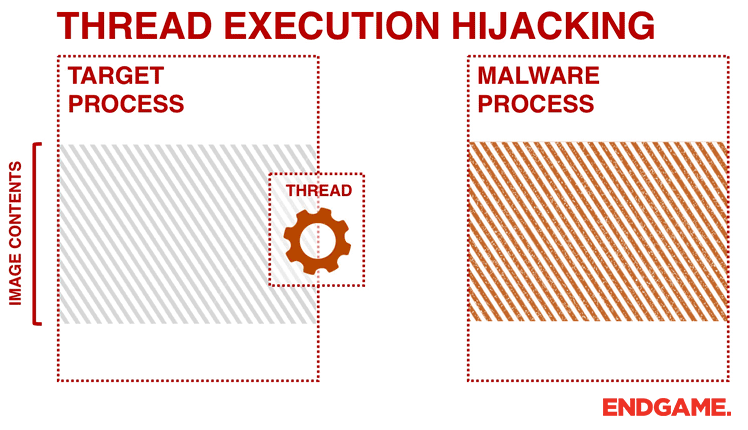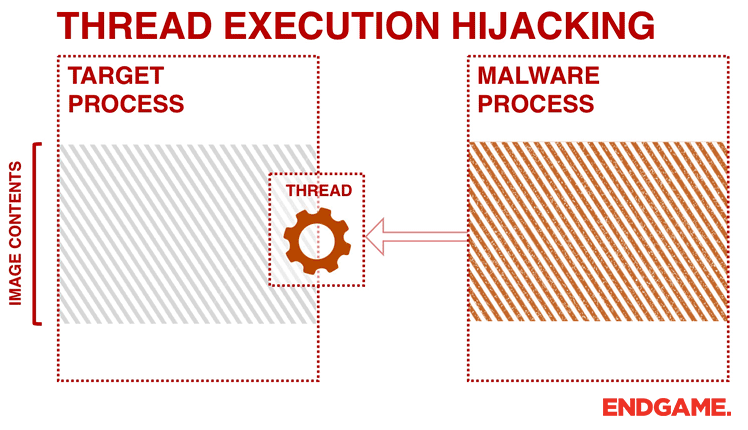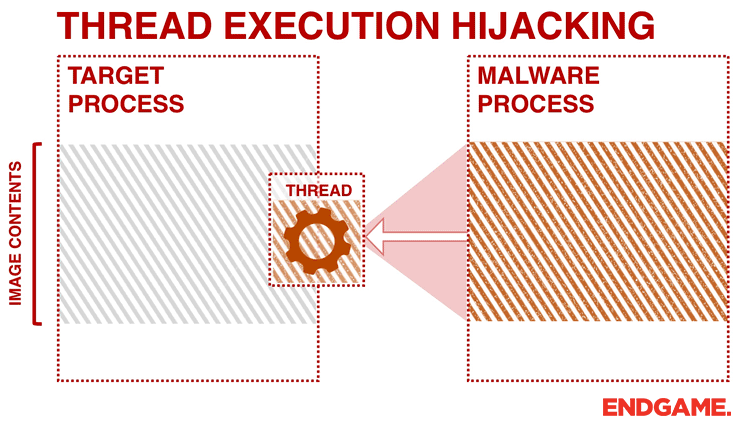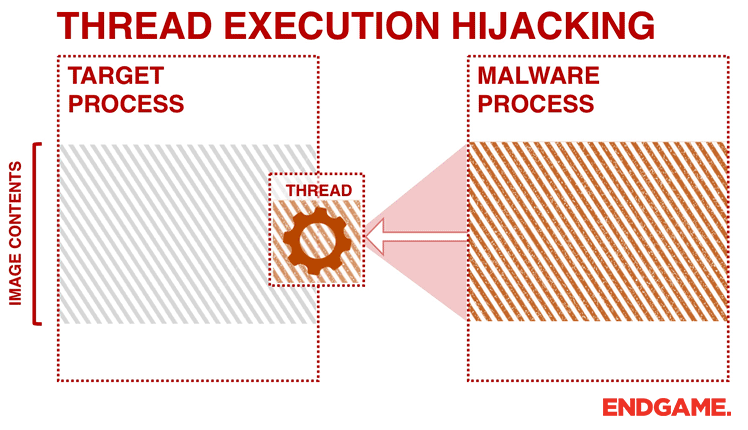
Ten process injection techniques: A technical survey of common and trending process injection techniques | Elastic Blog

Data-Driven Quantitative Intrinsic Hazard Criteria for Nanoproduct Development in a Safe-by-Design Paradigm: A Case Study of Silver Nanoforms | ACS Applied Nano Materials

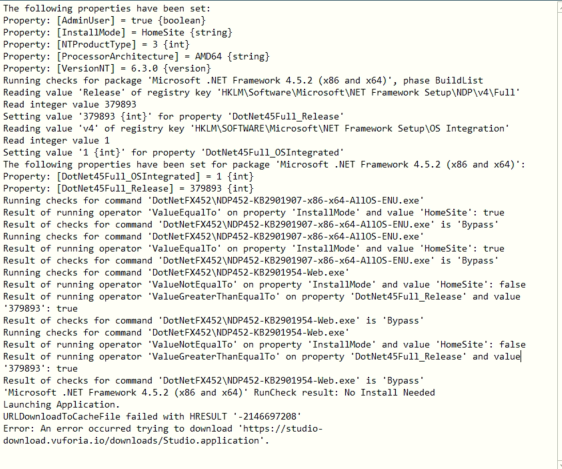
Technical Advisory: Dell SupportAssist Local Privilege Escalation (CVE-2021-21518) | NCC Group Research Blog | Making the world safer and more secure
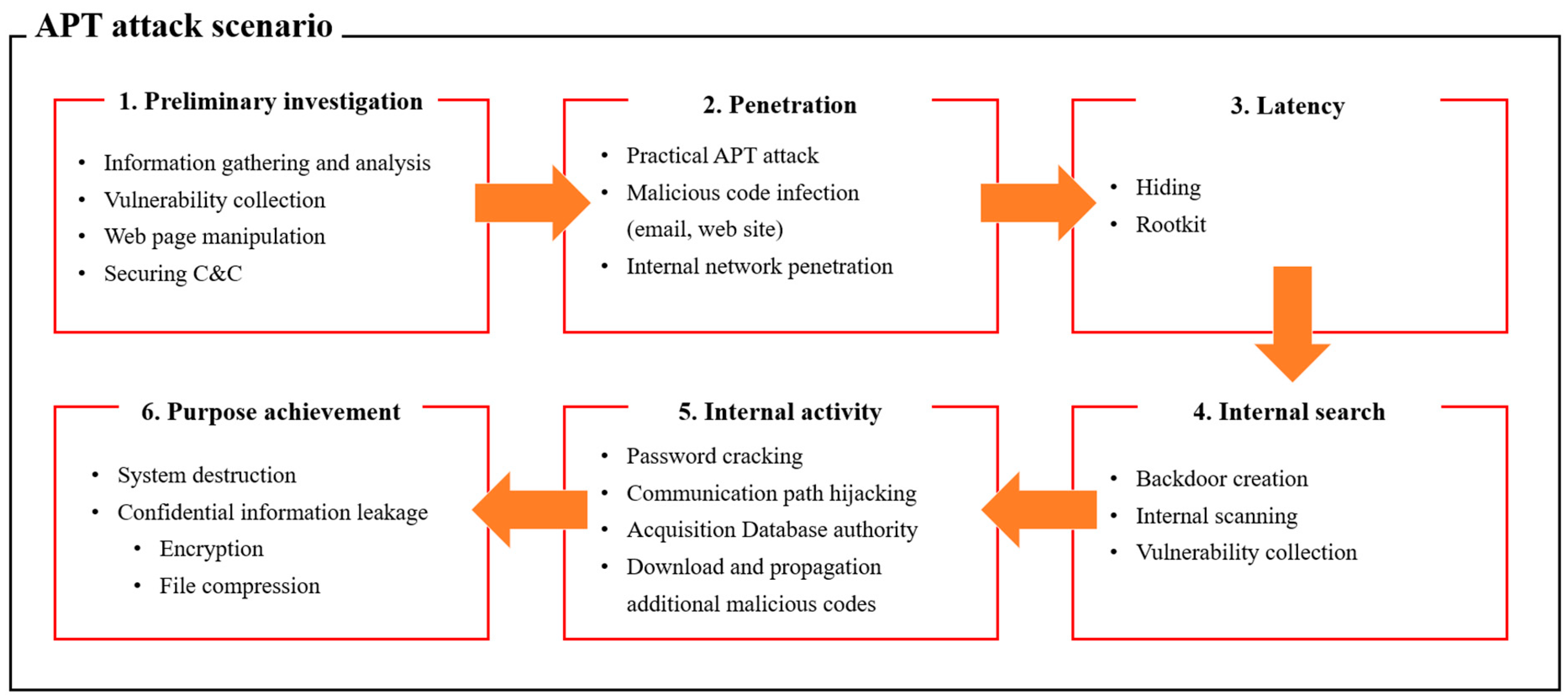
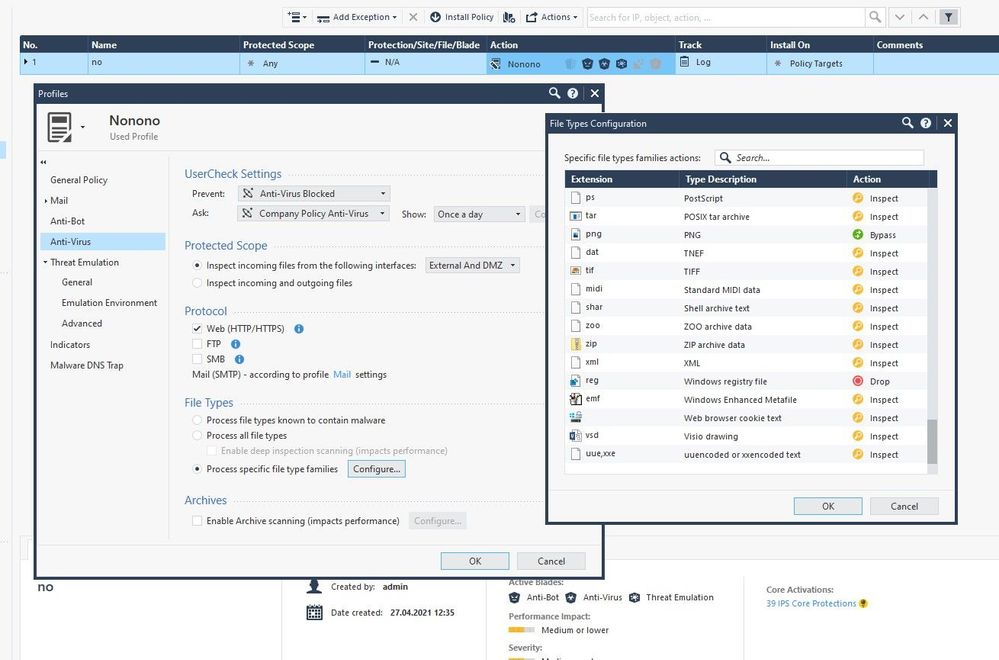
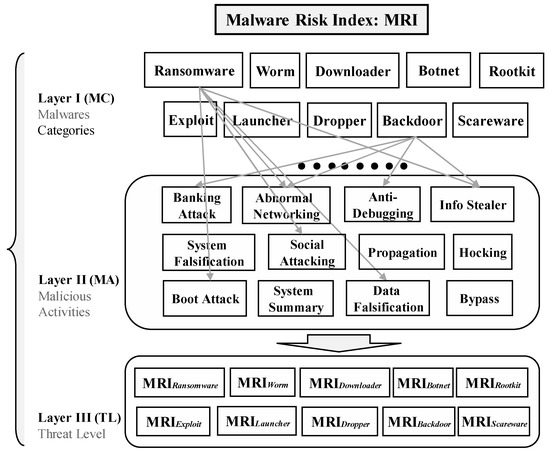
Applied Sciences | Free Full-Text | Classification and Analysis of Malicious Code Detection Techniques Based on the APT Attack
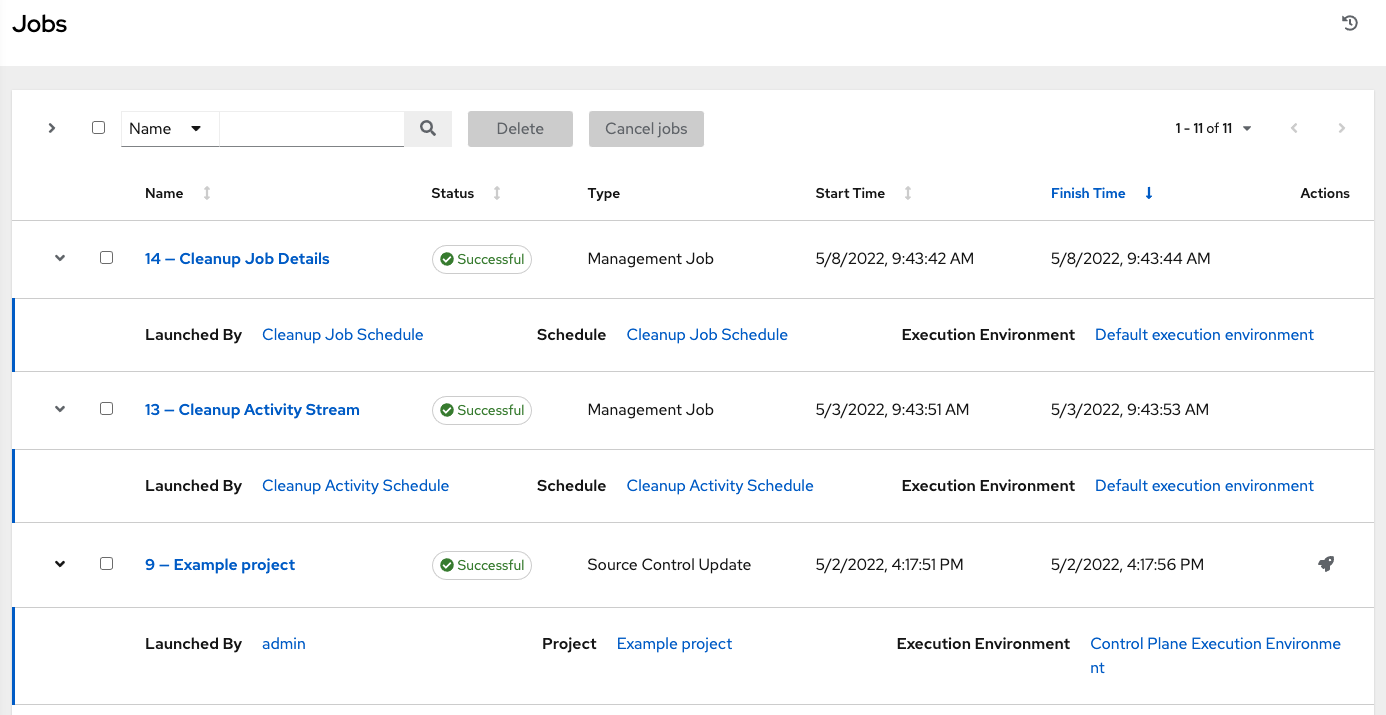
Chapter 25. Jobs in automation controller Red Hat Ansible Automation Platform 2.4 | Red Hat Customer Portal

Orthophosphate and Sulfate Utilization for C–E (E = P, S) Bond Formation via Trichlorosilyl Phosphide and Sulfide Anions | Journal of the American Chemical Society